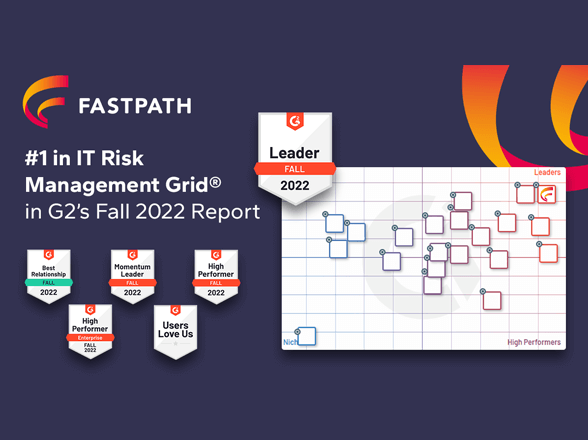
Why Choose Fastpath?
Our intuitive cloud-based platform seamlessly integrates identity governance and GRC into one sophisticated yet easy-to-use solution. Effortlessly automate, control, and monitor access - from applications down to individual data records to dramatically reduce risk and compliance costs.


Simple by Design
Identity, security and access controls are essential for today’s enterprise. The growing complexity of regulatory requirements -- Sarbanes-Oxley (SOX), HIPAA, FISMA, GDPR -- means you must constantly manage security and access risk across business applications, systems, and platforms.
But it doesn’t have to be complex. Fastpath can help you achieve this efficiently and effectively.
By providing a consolidated view for complete visibility into user permissions and security settings, we help you take control of your application risk and ensure that the right people are accessing the right information for the right reasons.
We give businesses confidence in compliance and trust in security.
“This is now our standard, and to help everyone meet that standard, we are providing Fastpath as the tool to achieve that goal. Fastpath now regularly provides a list of users, a list of security roles, and a list of SoD conflicts which is something we did not have previously. It is saving us a lot of time.”
Tim Dewson Group IS Manager , Watson-Marlow Fluid Technology Solutions
“As we were doing the implementation, our concern was that when we were in the Intacct environment, system limitations required a lot of extra SoD conflict rule sets to monitor and a lot of extra manual controls. With Oracle, there’s a lot more system functionality that prevents that, but we were still concerned about going into the new system and missing something. But Fastpath provides an off-the-shelf standard ruleset for Oracle, which has proven to meet all of our needs. What you’re hoping for with this kind of software is that there’s nothing left to chance, and that is exactly what we have experienced with Fastpath.”
Michael Higgins, Sr. Manager , SOX Compliance, The Trade Desk
“The implementation story here is a short one. It literally required getting the connections with Dynamics 365 and other components (third-party solutions, etc.) figuring out and then importing the data. Honestly, it can happen in an afternoon.”
Nick Tavenier , ERP Systems Analyst, Pattern Energy
“Having Fastpath Assure has been a lifesaver. There are some native security reports available in Microsoft Dynamics AX but without Fastpath’s capabilities, it would have been a painful, time-consuming process. We were especially pleased that Fastpath was able to address additional items required by our auditors that were not part of the standard delivered rule-set and directly map the rules from our previous ERP to Microsoft Dynamics AX.”
Jeff Zuniga , Group Manager for IT Process and Measurement, Flow International
“It is very apparent that the application was written by auditors for auditors. Audits are much faster and cleaner. I gave them access to the reports they needed, which helped them get their testing done much more efficiently compared to the past. So, this was one area where there was big ROI right off the bat.”
Ivan Ng , Application Security Audit Manager, Hearst
Who is Fastpath for?
.png)
Audit and finance
Fastpath’s platform was designed by auditors who understand the complexity of securing business application access. That’s why we created a solution that reduces the time, cost and complexity associated with audit processes and reporting to prove compliance.
.png)
Compliance
Fastpath has global partnerships with many of the world’s audit and technology firms, and critical business application tools like AuditBoard, Workiva, ServiceNow, Jira, Active Directory, and more so you can put Fastpath at the center of your GRC program.
.png)
Information Technology
Cloud-based and automated, Fastpath enables you to manage identity and access for all applications, ensuring consistency across systems, geographies, and business units. You can control onboarding, manage identity lifecycle and resolve SOD conflicts quickly.
.png)
Information Security
Orchestrate all aspects of your identity and access management from one platform. We help you take control, ensuring adherence to security policies and frameworks, as well as a consistent set of controls across your organization.








Supporting Your Business.
.png?width=588&height=440&name=complete-identity-security%20(2).png)
Complete Identity Security
Fastpath makes it efficient and cost-effective to discover, manage, and secure identities across your enterprise. From the moment you hire in your HR system, we enable you to automate access as users join, move within, or leave the organization. Vast interconnectivity, rich user context data, and customizable workflow simplifies the management of all identities and access, continuously monitoring and responding to changes.
Cross Application Access Controls
Today’s business operates with a variety of applications. Shouldn’t your access governance tools do the same? Perform securable-object level analysis across your critical business applications without spreadsheets or manual intervention. Fastpath analyzes access risk across applications by user, role, domain or privilege, from the enterprise level down to the deepest level of security. Whether you need to manage Separation of Duties (SOD) conflicts or perform data access risk analysis, Fastpath gives early warning of potential issues, helping prevent the cost and headache of control failures, fraud, or data breaches.
Automated Certification
Keep track of who has access to your critical business applications with Fastpath’s certification. We enable you to certify user identities and access. Define owners and reviewers with ease, schedule periodic certification reviews, and sign off for different types of access. Perpetual schedules combined with both complete and incremental review options and reminder settings means your continuous monitoring happens without you having to intervene.
Change Tracking
Fastpath was designed by auditors to detect and reduce both potential and actual risk. Define the changes you want to track with the change tracking product, or leverage out-of-the-box templates that focus on high-risk areas. Detailed analysis allows you to track changes to both transactions and master data, including who made the change, as well as before/after values. Carry on with business, confident that everything is under control.
Case Studies

Arrow S3
Purchased by a public company, S3 had to quickly become SOX compliant. Fastpath assists. . .

Diversified Manufacturing Company in Grocery, Retail, Electronics and Third Party Logistics
Read how you can save on licensing costs during an implementation
Hamamatsu
Read how Hamamatsu Corp, a global, publically traded company, simplified audits in Dynamics AX. ...
97%
of ROI within 12 months
+95%
of Customer Retention
Our Integrations
Fastpath makes it easy for you to integrate the tools, systems and applications that you use every day across your business.

















Using Zero-Trust And Least Privilege Access To Overcome Threats
Technology Record covers news and articles about Microsoft technology for enterprise businesses. In the Summer 2022 edition, the cover story is about Overcoming Threats, discussing how companies can protect their data and networks. And it comes down to people and zero-trust strategies.
Resources
 Whitepaper
Whitepaper
Managing Identity and Access Controls Across Multiple Applications
Learn best practices companies should consider when dealing with the evolving business application security landscape.
Learn more Whitepaper
Whitepaper
NetSuite Change Management
This whitepaper examines the native NetSuite functionality available to deploy effective change management in a NetSuite environment.
Learn more Whitepaper
Whitepaper
30 Tips And Tricks For Dynamics 365FO Security
Included in this whitepaper are tips for specific security settings, improving security via setup, process change options, mitigation tools, and principles for improved security going forward.
Learn more